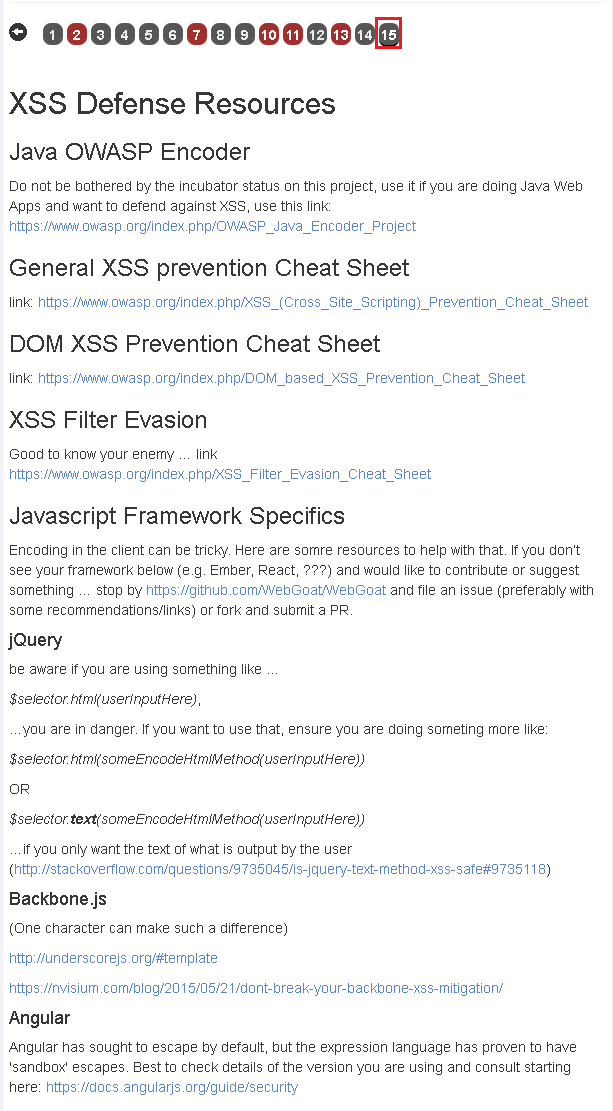
Owasp Sql Injection Prevention Cheat Sheet
SAP Cloud Platform, API Management offers many out of the box API Security best practices which can be customized based on your enterprise requirements. These API Security Best Practices includes security policies for Authentication and Authorization, Traffic Management and many more. Alcatel one touch 8008d driver download for windows.
For more information please see the Input Validation Cheat Sheet. Related Articles. OWASP article on LDAP Injection Vulnerabilities. OWASP article on Preventing LDAP Injection in Java. OWASP Testing Guide article on how to Test for LDAP Injection) Vulnerabilities. Authors and Primary Editors. Ben Weintraub - Ben@bluetalon.com. Jim Manico - jim. The OWASP Cheat Sheet Series was created to provide a set of simple good practice guides for application developers and defenders to follow. Query Parameterization Cheat Sheet Introduction. SQL Injection is one of the most dangerous web vulnerabilities. So much so that it's the #1 item in the OWASP Top 10. It represents a serious threat because SQL Injection allows evil attacker code to change the structure of a web application's SQL statement in a way that can steal data, modify data, or potentially facilitate command injection. 20 SQL Injection Prevention Cheat Sheet 139. V Draft Cheat Sheets 249 32 OWASP Top Ten Cheat Sheet 251 33 Access Control Cheat Sheet 252. SQL Injection Prevention Cheat Sheet; JPA Symptom. Injection of this type occur when the application use untrusted user input to build a JPA query using a String and execute it. It's quite similar to SQL injection but here the altered language is not SQL but JPA QL. Use Java Persistence Query Language Query Parameterization in order to prevent injection.

OWASP Top 10 that represents a broad consensus about the most critical security risks to web applications lists Injection attacks as one of the Top 10 web application security attack. SQL Injection attacks is a type of injection attack which is used by malicious users to gain access to or alter database information available only to the REST APIs, such as:-


- access sensitive data like user names and passwords.
- corrupt or delete data in the database.
Using Regular Expression Protection Policy from SAP Cloud Platform API Management SQL injection attack can be easily detected. In this blog we will extend the previous blog of Log all API Interactions to detect the usage of SQL commands like drop table, insert, shutdown or update, in URL patterns, query parameters etc. For the complete list of SQL commands, refer OWASP SQL Injection Prevention cheat sheet.
Prerequisites
- SAP Cloud Platform API Management tenant.
Launch API Portal
- Logon to your SAP Cloud Platform, API Management account (say https://account.hanatrial.ondemand.com/cockpit).
- Navigate to the Services tab, search for API Management service tile and click to open API Management service.
- Click on the link Access API Portal to open API Portal.
SQL Injection Threat Protection
In this section we would describe the usage of the Regular Expression Protection Policy to detect the usage of SQL commands like drop table, insert, shutdown or update from OData query parameters like $format, $skip, $filter, $top and $count.
- Navigate to the Define from the hamburger icon, then select the tab APIs. Select the API Proxy to which API Rate limiting was applied.
- Click on the Policies button of the selected API Proxy.

- Click on the Edit button from the Policy designer and Select PreFlow from the ProxyEndPoint section and then click on the + button next to the Regular Expression Protection Policy available under theSecurity Policies segment.
- In the Create policy screen specify the policy name say checkForCodeInjection and then click on the Add button.
- Select the newly added checkForCodeInjection policy then add the following policy snippet.
- Click on the Update button to save the Policy changes
- Click on the Save button to save the changes to API Proxy.
With this we have successfully applied a Regular expression protection to detect SQL commands like drop table, insert, update, shutdown passed in the Query parameters, URL patterns or request body.
Finally testing the flow
- Navigate to the Test tab from the hamburger icon
- From the APIs list search for the API Proxy that you would like to test say GatewayServiceRestrictedAccess and then click the API to test.
- Click on the Authentication: None link and select Basic Authentication to set the user credential to connect to the SAP Gateway ES4 system
- Enter your user credential to the SAP Gateway ES4 system and click on the OK button
- Click on the Url Params button. Enter $format as URL parameter name and drop table as the parameter value and then click on the Send button
- Since a SQL command drop table was passed in the query parameter, it would detected by the Regular Expression Protection Policy and then an error would be returned.
Owasp Csrf Prevention Cheat Sheet
- Change $format URL parameter value to json and then click on the Send button.
- Since the request is within the given limit defined in the Regular Expression Protection policy, the call would be successfully passed by the SAP API Management to the SAP Gateway system and the response returned.
Further Reads
Owasp Sql Injection Prevention Cheat Sheet
- For more blogs on SAP Cloud Platform API Management visit us at SAP Community
